Data Collection
TrustFactor is a transactional authentication solution for web services and APIs that require strong authentication before authorizing a sensitive transaction to be executed. In this manner, TrustFactor only stores information that is shared between the integrating application and the TrustFactor services for authentication purposes.
In order to provide the aforementioned service, we are required to collect and store some personal information about the user.
Data Usage and Purposes
All personal or sensitive information gathered is used only for risk analysis and fraud detection/prevention purposes.
Profile Association
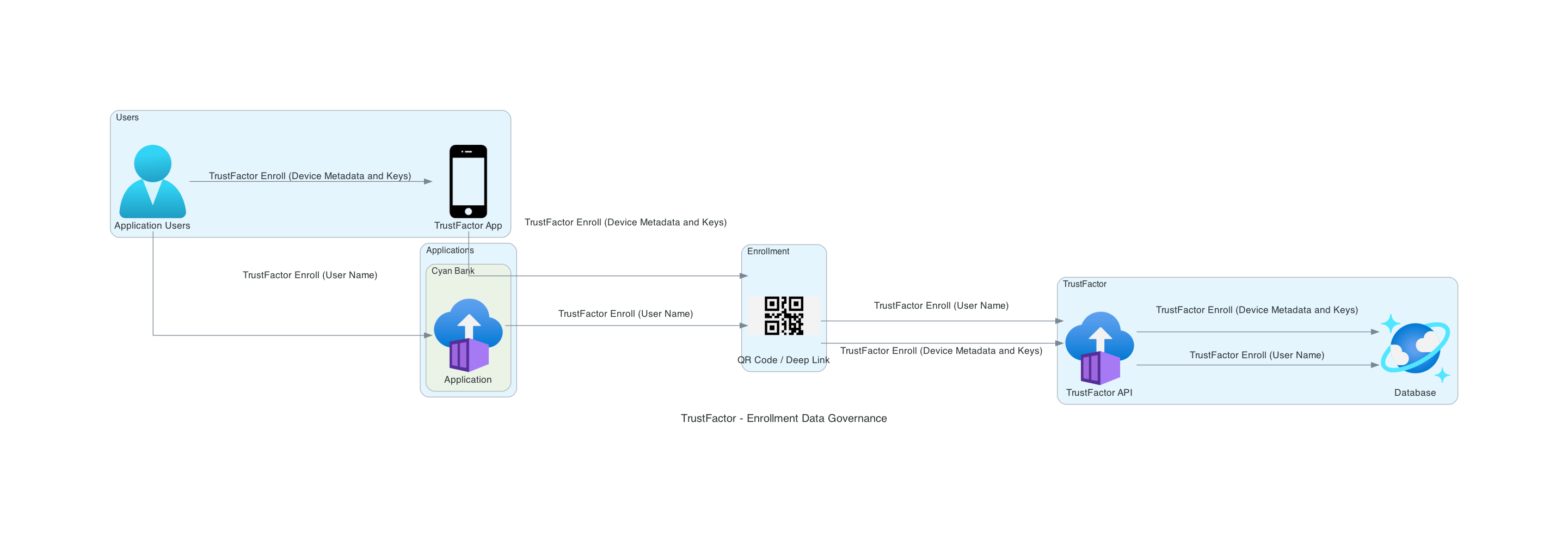
Before a TrustFactor App can be associated with an application profile, it must first register itself with the TrustFactor services using the API. This sends anonymous information about the device and generates a unique identifier and key pair for that given installation on that device. If a user removes and re-installs the application, a new unique identifier and key pair is generated.
After the user has installed the TrustFactor App, they are now ready to generate an enrollment token with the integrating application (e.g. Cyan Bank, our ficticious demonstration application). The user will then proceed with the enrollment process in Cyan Bank Application and obtain a registration token that, when scanned via QR code or used via deep-link on mobile devices, links the device information to the profile information.
When the Application generates the enrollment token for a given application profile, the application must send the "Username" for the profile registered, which is then shown to the user on the TrustFactor App. In some applications, this "Username" may contain the first, last or full legal names of the person. See the Handling Sensitive / Personal Data section for more information.
When profile association occurs, the location of the device where the TrustFactor App is installed is also stored for security and audit purposes.
Information about the device where the TrustFactor App is installed is also gathered for security and audit purposes. This information may include, but is not limited to, the Device Manufacturer, Device Model, Operating System Type, and Operating System Version.
Transactional Authentication
Before a transaction authentication request is issued to the TrustFactor App, it may be subject to risk analysis. This transactional risk analysis may leverage the geolocation of the devices currently associated with a given application profile. For privacy reasons, this validation only uses the last known location of the device and does not keep historical records of the device's geolocation. In addition, whenever possible, we use the least precise geolocation input available that fulfills our functionality requirements.
We may also use historical behavioral analysis of the transactional pattern for a given application profile in order to assess the risk of a given transaction.
Transaction Signature Proofs
Applications that integrate with TrustFactor can obtain signed proof documents containing the decision made by the user using the device where TrustFactor App is installed. This document contains metadata about the device that signed the approval or rejection, including but not limited to: its approximate geolocation, device manufacturer, device model and public key information.
Handling Sensitive / Personal Data
Applications that wish to send sensitive or personal data for user authorization using transaction authentication requests, may do so using parameters specifically designed for this purpose.
It is of the responsibility of the application's developers to thoroughly mark all sensitive data by using the provided methods to do so, as it is impossible for SecuritySide, CyberSecurity Services S.A. to determine given the generic approach to the application's interface, and therefore cannot be liable for the application's mislabeling of personal data.
All data marked as sensitive or personal is stored with careful considerations:
- in isolated storage in a given geo-location to comply with proper data jurisdiction requirements
- allows applications to remove this data at the request of a user to comply with legal requirements in certain jurisdictions
- all data is encrypted at rest and in transit
- all data access is logged for auditing and security purposes
Data Sharing
We do not currently share personal or transactional information with third parties.
We do use third-party services for logging, analytics and crash event management that require information about the user to be shared with them, please refer to the Privacy Policy section for more information.
GDPR
In this section we provide the mechanisms implemented to comply with the EU's General Data Protection Regulations.